A New Way of Distributed Networks
From the origins to Tezos as a P2P network
Tezos is a peer-to-peer (P2P), open-source blockchain protocol with which you can execute transactions and deploy smart contracts.
To understand whether blockchain technology in general and specifically Tezos is a good fit for your project, it is important to understand where it comes from and what is driving it.
The origin
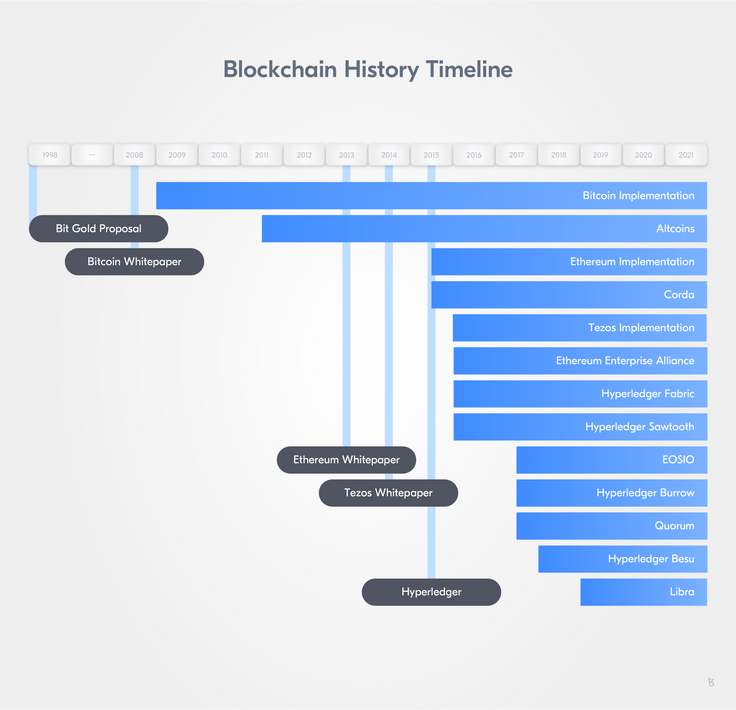
Important groundwork was laid in the 1980s and 1990s for what will later be known as blockchain technology. Although the technology itself was not created until 2008, researchers from different fields in computer science and cryptography proposed solutions to many problems regarding security, transparency, and trust. All of them contributed to the development of the first large-scale, successful public blockchain network, Bitcoin.
In 1991, two research scientists, Stuart Haber and W. Scott Stornetta, identified a problem: How can it be ensured that digital documents are authentic and changes to them are tracked in an immutable time-stamped manner? In How to time-stamp a digital document, they worked on the concept of append-only, cryptographically secured logs. With their work, the foundations of what much later becomes blockchain technology were laid.
Then in 1994, when computer scientist Nick Szabo first described the concept of smart contracts, Szabo intended to minimize the need for trusted intermediaries. In 1998, Szabo argued in favor of a decentralized digital currency; he proposed Bit Gold, a conceptual predecessor to Bitcoin. Szabo proposed Proof-of-Work as a consensus algorithm to solve cryptographic puzzles in a P2P network with Byzantine Fault Tolerance. The solutions are also linked together by a "hash chain" (See: Moskoy, Phillip (2018): What Is Bit Gold? The Brainchild of Blockchain Pioneer Nick Szabo). Although Bit Gold was never implemented, many perceive it as being the direct ancestor to Bitcoin.
Also in 1998, Bruce Schneier and John Kelsey proposed a computationally cheap way to safeguard sensitive information and allow for computer forensics with secure audit logs by using hashing, authentication keys, and encryption keys (See: Schneier, B. & Kelsey, J. (1998): Secure Audit Logs to Support Computer Forensics).
As we can see, these intellectual predecessors identified elements that are essential to blockchain technology.
The new millennium arrived and on October 31, 2008, Satoshi Nakamoto called for a P2P system for a digital currency that would allow online payments to be sent directly from one party to another without going through a financial institution or requiring any other third party involvement. This sounds familiar for a reason: Nick Szabo had already mentioned a currency that would depend minimally on third parties, Bit Gold. However, Satoshi’s paper differed significantly - not only because of the name difference between Bit Gold and Bitcoin. The Bitcoin Whitepaper also proposed a data structure for the Bitcoin blockchain and laid out the decentralized consensus mechanism. It became the first large-scale, successful public blockchain network.
As the first blockchain network launched, several were to follow.
In 2014 Vitalik Buterin started what is now known as the second wave of blockchain technology by publishing the paper underlying the Ethereum blockchain protocol, A Next Generation Smart Contract & Decentralised Application Platform. Beyond a distributed ledger, the Ethereum Whitepaper proposed the development of a distributed computation platform. The project raised roughly $20 million in one of the most successful crowdfunding campaigns up to that point. The first public network was up and running in 2015. At the same time, it spawned the first managed blockchain network approach when the company Eris forked a version of Ethereum and expanded it to implement a layer of permissions, as well as making it easier to deploy custom, access-controlled networks. In 2017 the Ethereum Enterprise Alliance was formed as an industry consortium to adapt Ethereum for enterprise use.
As soon as it became clear that the technology presents a very attractive base infrastructure for payments, other groups and organizations adapted the technology for their purposes or developed new approaches using the same basic principles but adapting them to more traditional use cases. Late 2015 saw the establishment of the Hyperledger Project from the Linux Foundation, an industry consortium with a focus on enterprise blockchain technology for managed networks and business applications. Following the Hyperledger endeavors, R3, first a bank consortium that later became an enterprise software company, launched Corda, an open-source blockchain platform.
This brief background introduces the vibrant community and fast-paced evolution of the space from which Tezos would emerge. In August 2014, L.M. Goodman published the Tezos Position Paper followed by the Tezos Whitepaper on September 2nd of the same year. By the Fall of 2014, a group of developers tasked with developing the protocol had produced a crude but functional network shell. In 2017, the Tezos Foundation raised $232 million in one of the biggest initial coin offerings (ICO) that year. The network launched in June 2018 its Betanet and later in September its Mainnet.
In 2019, two protocol upgrades followed: Athens and Babylon. Both upgrades aimed at making the native coin, tez (XTZ), more attractive. With Babylon, simple smart contracts development, a more robust version of the consensus algorithm, and improvements on the delegation process were promoted. In March 2020, Carthage followed - an update to allow for complex application development and improve the accuracy and security of the blockchain. Delphi and Edo followed in September 2020 and February 2021. Later, in May 2021 Florence came along, which was followed by Granada later that year in August. Before the year ended, a third upgrade, Hangzhou, went live - the 8th upgrade to the Tezos protocol. For 2022, a new upgrade called Ithaca is planned.
Delphi tackled gas consumption, storage costs, and smart contracts to continue optimizing the network. Edo included, next to some bug fixes, improvements to performance and gas consumption to lower gas fees, as well as some changes to the upgrade process, and the introduction of sapling for shielded transactions and tickets.
The three updates introduced in 2021 are envisioned to further improve the protocol for usage. Florence brought with it further gas optimization, introduced a doubled maximum operation size, improved performance, two new normalization RPCs, a depth-first execution order for inter-contract calls, and a more reliable and streamlined amendment process by deactivating the testchain feature in the Testing Period. The Florence upgrade can be seen as a reaction to an increase in network activity observed after Delphi. This becomes clear when taking a closer look at the number of contract calls on Tezos: Until February 2021, the number of contract calls had been increasing but remained less than 100,000 calls per month. In March, the number had risen to ~ 360,000, and later in April 2021, the contract calls surpassed 1.3 million. The Granada upgrade not only included bug fixes and improvements such as further measures to reduce gas consumption, but also an upgrade of the consensus algorithm from Emmy+ to Emmy* to achieve smaller block times and faster finality and liquidity backing. With liquidity backing, decentralized liquidity between tez and tzBTC is freed by minting tez every block and depositing it in a certified product marketing manager (CPMM) smart contract. Later, the Hangzhou protocol upgrade is the 8th protocol upgrade for Tezos and was envisioned to prepare a consensus upgrade in 2022 to Tenderbake. Hangzhou added a timelock to allow smart contracts including counter-measures against Block Producer Extractable Value. In addition, developers can register Michelson expressions as "constants" to reference them in contracts, and Michelson on-chain views are possible to provide smart contracts with a new mechanism for contract calls, so to say smart contracts can now read the storage of other contracts. The use of storage was further optimized with faster access to caching results, which also increases the throughput of the Tezos protocol. The upgrade also included context flattening to increase the processing of operations and blocks and some changes regarding liquidity baking.
Want to take a closer look at past upgrades, the changes they brought, and even discover their related merge requests? Check out the Tezos documentation.
Tezos: A P2P network
Tezos is a blockchain network that allows for peer-to-peer transactions. So, let's take a short look at P2P networking and its relation to distributed networks.
A peer-to-peer (P2P) network has a distributed architecture. All participants, called nodes, are equal. Understood as equality is that all participants are equally privileged and equipotent. Each node connects to a limited number of other nodes, which are commonly referred to as its peers. Peers make resources like computing power and network bandwidth available to all peers in the network.

In P2P networking there is no central server, storage, or authentication of users. Peers can be understood as file servers and clients at the same time. If a node cannot answer a request, it will forward it to some or all of its known peers. This combination of client-server roles opens up resilience and scalability gains.
Why is this?
Resilience is improved because one node being down does not translate to a service disruption or the whole network stopping to work. Scalability is gained because each new node serves as a new client but also a server.
Upholding security in P2P networks - A challenge
Security is challenging in P2P networking for two reasons:
- P2P software has to be downloaded to become part of the network, making it especially vulnerable to remote exploits;
- Because of interconnectivity, every peer has an equal network connection, a malicious participant could send incorrect requests or returns, as well as malware and corrupted data through the entire network. Other security risks are denial of service (DDoS) attacks, routing attacks, and routing network partitions.
Hashing, chunk verification, and a higher degree of encryption are means to mitigate security risks in P2P networks.
P2P networking & distributed networks
Networks can be decentralized, distributed, centralized, or a mix of both.
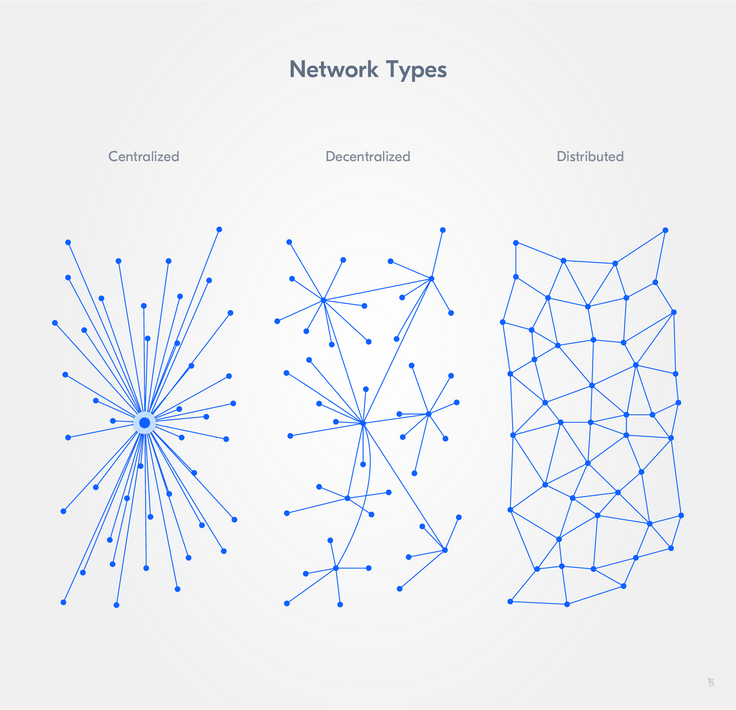
Broken down, a blockchain is a distributed ledger that records all transactions on the chain. Nodes in such a distributed ledger need to have a copy of said ledger, as well as constantly remain in communication with the network, which needs to continuously run without ever being offline. A blockchain requires a high degree of resilience and scalability due to it being a distributed P2P network with an expected growing number of nodes and processing necessities.
Tezos can be understood as such a distributed P2P network based on blockchain technology. As such, every node establishes and maintains a connection with the network, functions as more than a client of the network, and effectuates a number of operations.
Tezos implements a P2P layer. The node instantiates the P2P layer which is parameterized by the type of messages exchanged over the network (to support different P2P protocol versions and extensions) and the type of metadata for each peer. The metadata is used to compute a score for each peer that reflects the level of trust in the nodes. Policies can control communication between the node and peers based on the different scores (levels of trust) in those peers.
The P2P layer consists of a connections pool, the operations on those connections, and a set of workers. The worker pattern is used extensively and followed by the set of workers.
- Ethereum Whitepaper: A Next Generation Smart Contract & Decentralised Application Platform
- Goodman, L.M. (2014): Tezos: A Self-Amending Crypto-Ledger Position Paper
- Goodman, L.M. (2014): Tezos - A Self-Amending Crypto-Ledger Whitepaper
- Guenzburger, Eli (2021): Tickets on Tezos
- Kim, Christine (2019): Welcome to Athens: Tezos completes 'Historic' First Blockchain Vote
- Moskoy, Phillip (2018): What Is Bit Gold? The Brainchild of Blockchain Pioneer Nick Szabo
- Nomadic Labs (2019): Sapling integration in Tezos - Tech Preview
- Nomadic Labs (2020): Delphi: Official Rrelease
- Nomadic Labs (2021): Florence: Our Next Protocol Upgrade Proposal
- Nomadic Labs (2021): Announcing Tezos' 9th protocol upgrade proposal "Ithaca"
- Schneier, B. & Kelsey, J. (1998): Secure Audit Logs to Support Computer Forensics
- Satoshi Nakamoto: Bitcoin: A Peer-to-Peer Electronic Cash System
- Szabo, Nick (1994): Smart Contracts
- Tezos Agora Wiki
- Tezos Developer Portal
- Tezos Documentation: Athens
- Tezos Documentation: Babylon
- Tezos Documentation: Carthage
- Tezos Documentation: Delphi
- Tezos Documentation: Edo
- Tezos Documentation: Florence
- Tezos Documentation: Granada
- Tezos Documentation: Hangzhou
- Tezos Documentation: Ithaca
- Tezos Foundation (2019): Update: Week of 21 Octoberr 2019
- Tezos Foundation (2020): Tezos Teams Propose Latest Protocol Upgrade, Edo
- Tezos Info (2021): Hangzhou — New Proposal for Tezos’ Eighth Protocol Upgrade
- Tezos Medium Publication
- Tezos (2021): Florence, Tezos' Sixth Protocol Upgrade Goes Live, Bringing Further Gas Optimizations & More
- Wiser, Charlie (2019): Why Tezos is the Best Platform for Tokenized Assets